Phases of Insider Threat Recruitment: How Hackers Target Their Victims Insider threat policy template
If you are searching about Recruitment Ad Example We Are Hiring Sample - Growth Hackers you've visit to the right page. We have 25 Pictures about Recruitment Ad Example We Are Hiring Sample - Growth Hackers like 4 Malicious Browser Extensions That Help Hackers Target Their Victims, Phases of Hackers Module 1 Today s Threat and also Chinese state-backed hackers target PMOs, heads of nations - The Sunday. Here it is:
Recruitment Ad Example We Are Hiring Sample - Growth Hackers
 www.growth-hackers.net
www.growth-hackers.net
Iranian Hackers Using LinkedIn, WhatsApp To Target Victims
 www.databreachtoday.com
www.databreachtoday.com
linkedin victims hackers iranian target whatsapp using
Understanding Insider Threats: Insider Threat Dangers
 newscaler.com
newscaler.com
Chinese State-backed Hackers Target PMOs, Heads Of Nations - The Sunday
 sundayguardianlive.com
sundayguardianlive.com
Announcing Insider Threat Program Evaluator Training From The CERT
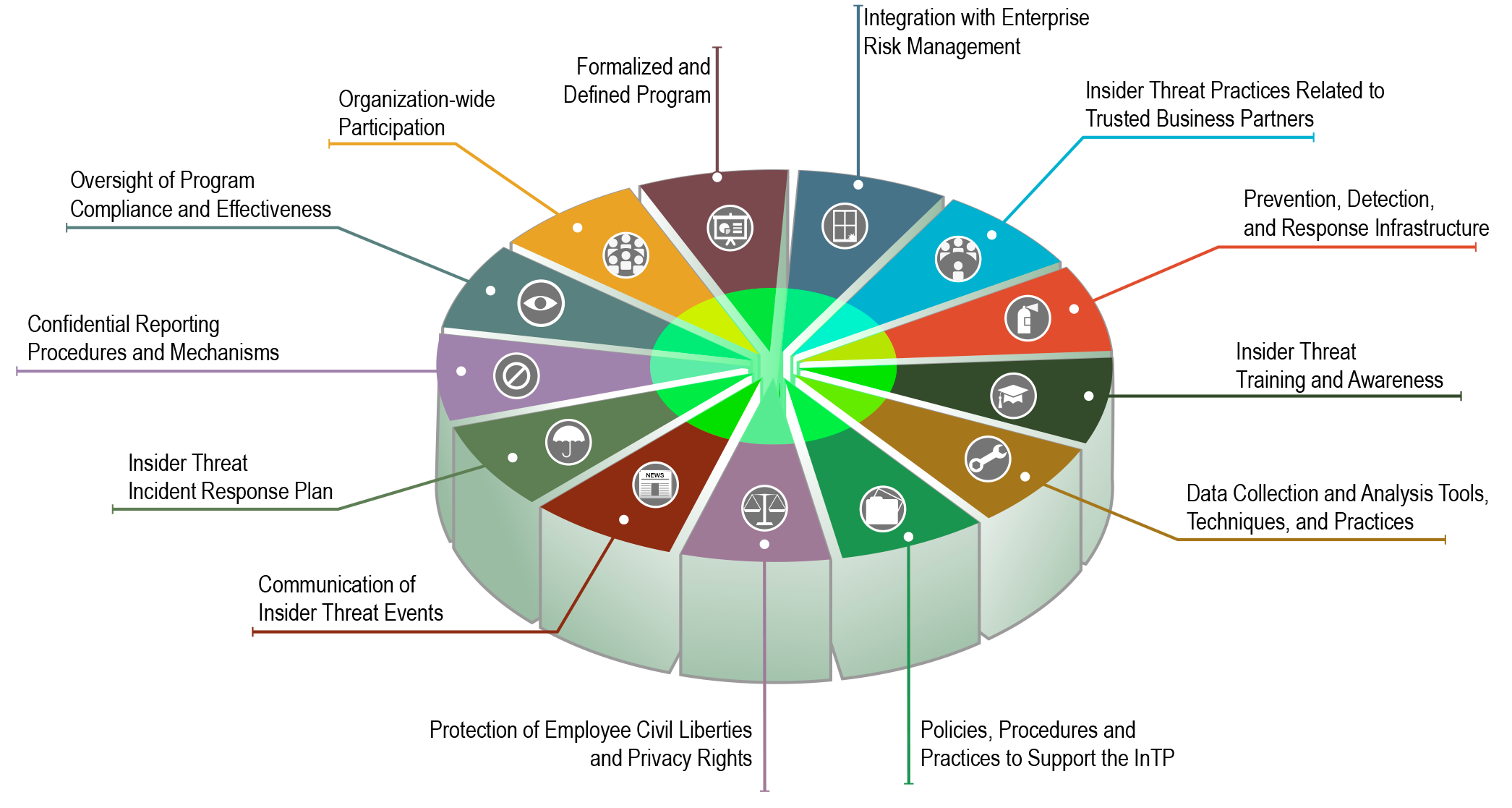 insights.sei.cmu.edu
insights.sei.cmu.edu
threat program evaluator announcing cert
Insider Threat Policy Template
 template.mapadapalavra.ba.gov.br
template.mapadapalavra.ba.gov.br
DMW Encourages Victims Of Illegal Recruitment, Human Trafficking To
 www.philstar.com
www.philstar.com
4 Malicious Browser Extensions That Help Hackers Target Their Victims
 www.makeuseof.com
www.makeuseof.com
extensions
Insider Threat: The Dangers Within | Mandiant
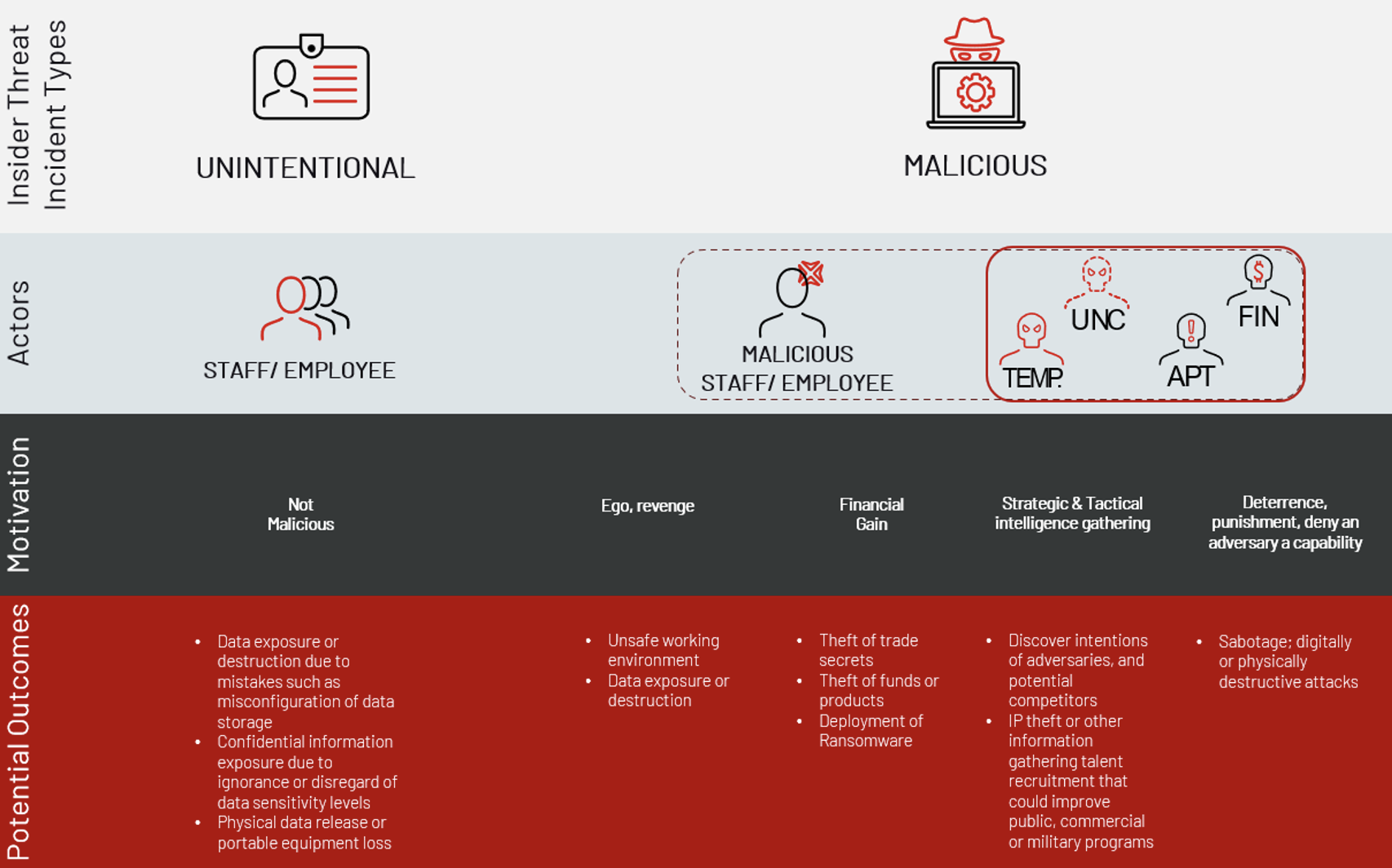 www.mandiant.com
www.mandiant.com
What Is Insider Threat Indicators | Types Of Insider Threats
 www.xcitium.com
www.xcitium.com
Hackers Use Recent Tragedies To Target Phishing Victims
 www.phishprotection.com
www.phishprotection.com
phishing victims hackers tragedies recent
September Is Insider Threat Awareness Month | SecurityOrb.com
 securityorb.com
securityorb.com
Malicious Insider Threat - CyberHoot
 cyberhoot.com
cyberhoot.com
insider malicious threat threats 2020
Insider Threat 3d Vector Anonymous Hacker Attack | CartoonDealer.com
 cartoondealer.com
cartoondealer.com
Insider Threat Awareness Quiz And Flashcards
 quizgecko.com
quizgecko.com
Threat Actor - CyberHoot Cyber Library
 cyberhoot.com
cyberhoot.com
threat cyberhoot malicious motivations
Insider Threats: Recruitment Tactics And TTPs | Flashpoint
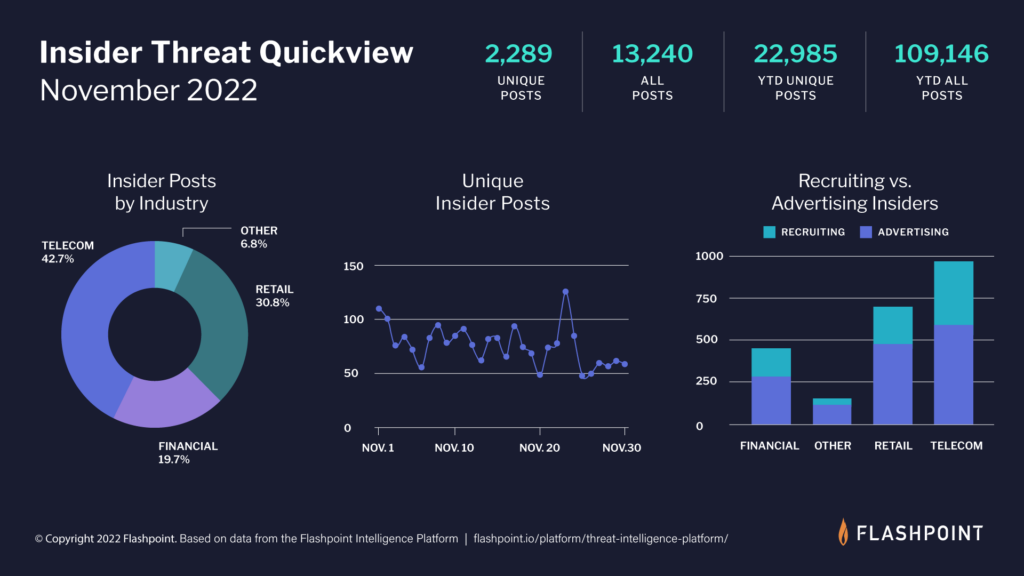 flashpoint.io
flashpoint.io
Hackers Target .NET Developers With Malicious NuGet Packages | Flipboard
 flipboard.com
flipboard.com
Target Email Scam - Business Insider
 www.businessinsider.com
www.businessinsider.com
target email scam insider business
Phases Of Hackers Module 1 Today S Threat
 present5.com
present5.com
Insider Threat: The Dangers Within | Mandiant
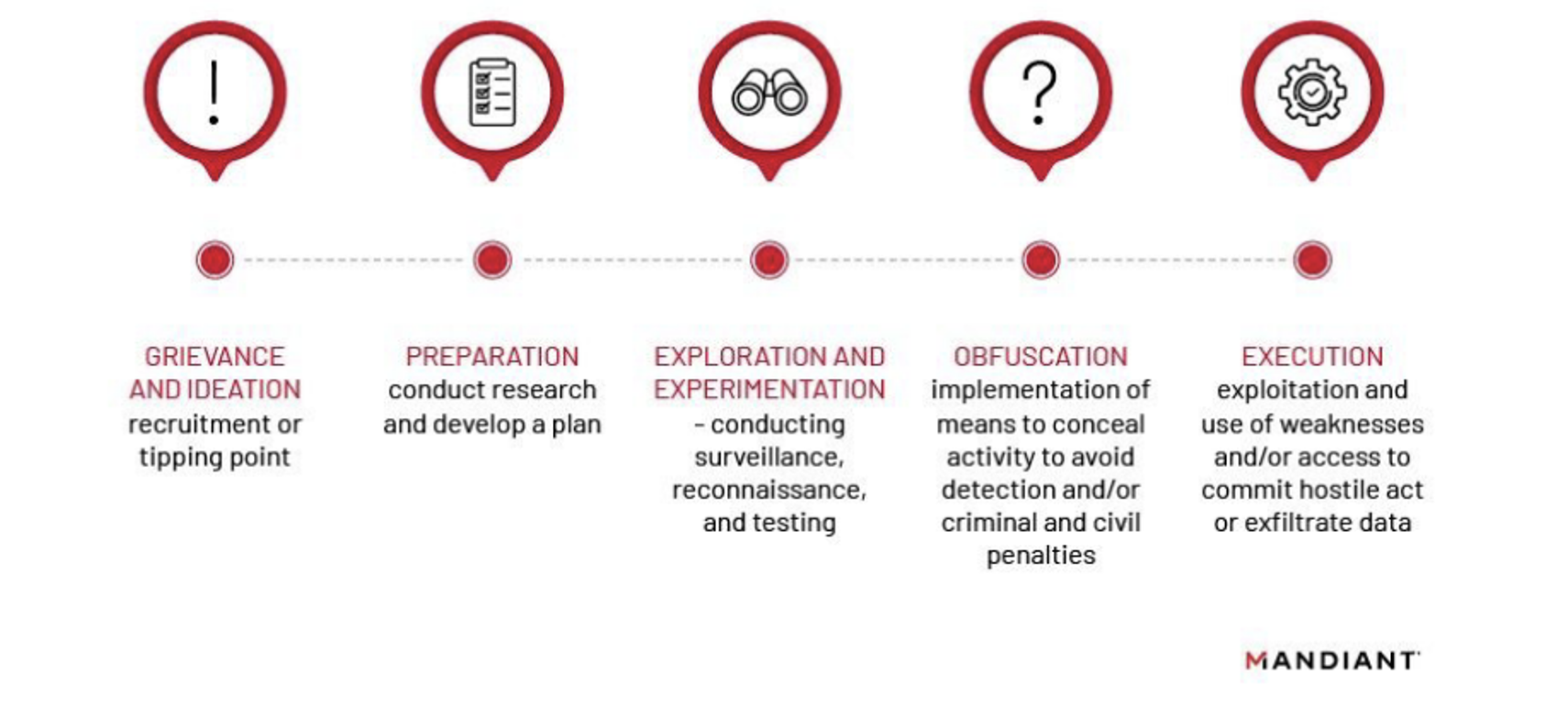 www.mandiant.com
www.mandiant.com
Phases Of Hackers Module 1 Today S Threat
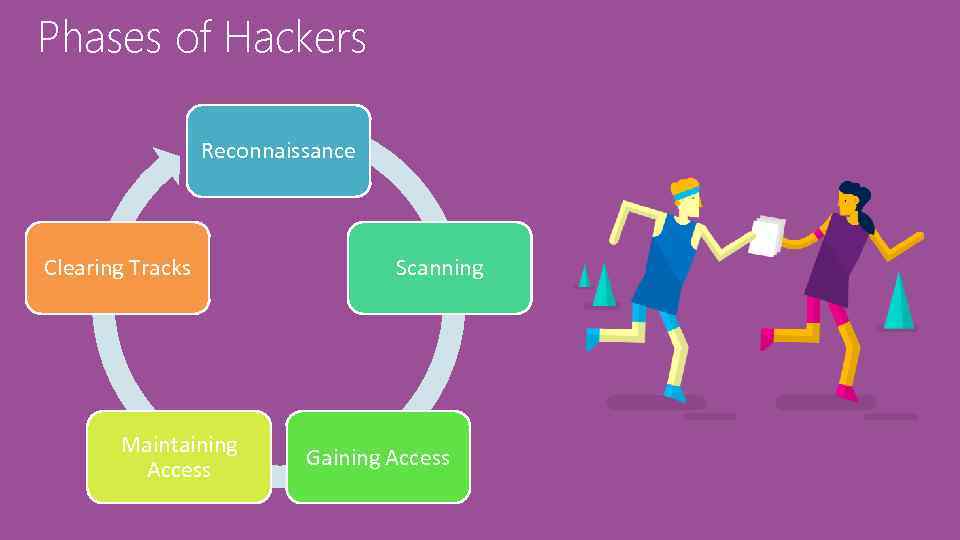 present5.com
present5.com
phases hackers module threat gaining advertisements
What Insider Threat Actually Looks Like | Fractional CISO
 fractionalciso.ca
fractionalciso.ca
How To Prevent And Detect Insider Threat - Adamo
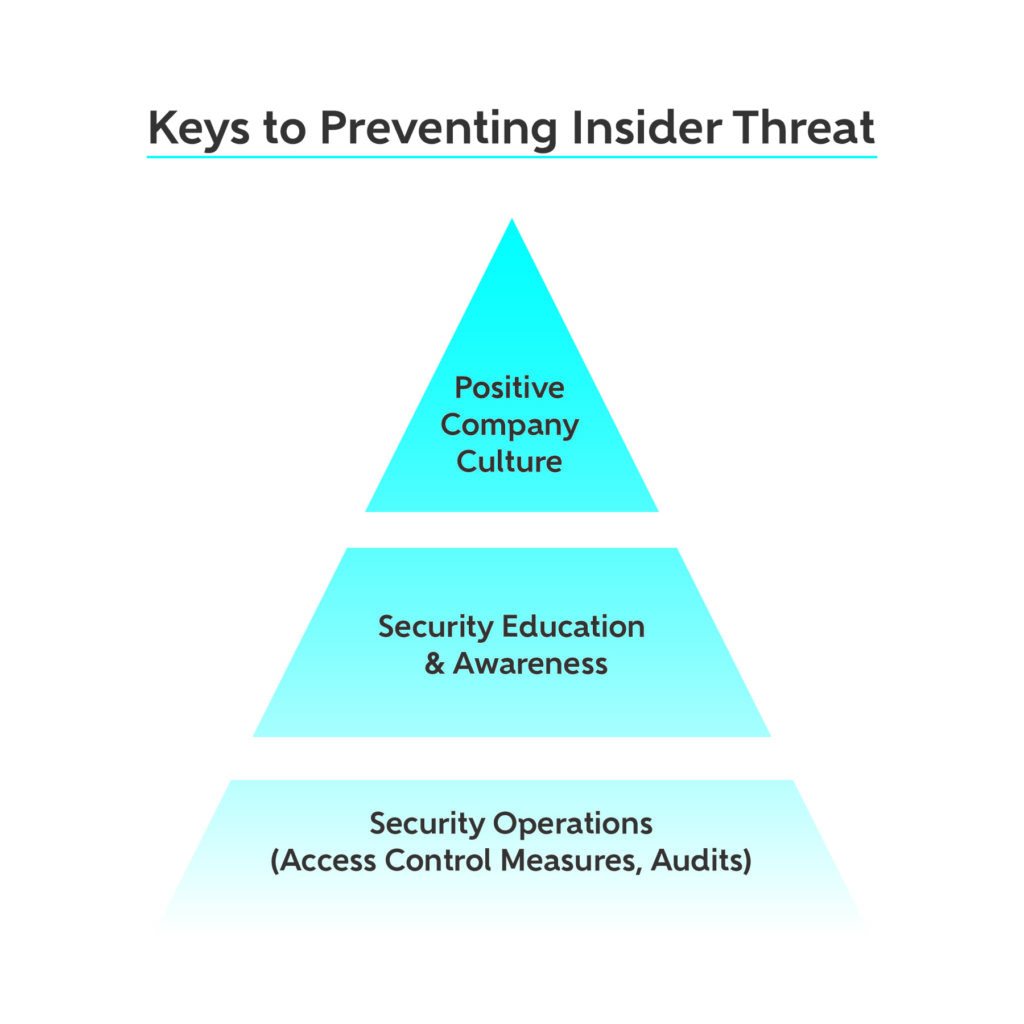 www.adamosecurity.com
www.adamosecurity.com
threat prevent detect
Threat Intelligence Monitoring - ACCi
 acci.com
acci.com
Dmw encourages victims of illegal recruitment, human trafficking to. Linkedin victims hackers iranian target whatsapp using. Insider threat: the dangers within